Shodan (noun): the world’s first search engine for Internet-connected devices.
Shodan (verb): To Shodan; I Shodan, You Shodan, We Shodan…do this, before an adversary does it for you.
You’ve likely read the story by now. An adversary used the Shodan search engine, “world’s first search engine for Internet-connected devices,” to seek results from large segments of the Internet for misconfigured commodity routers using FTP (port 21) to acquire sensitive documents from compromised systems. In short, the adversary was able to steal documents about Reaper drones because the victim didn’t set the FTP password on its Netgear routers (they were left as defaults), which allowed the adversary access. Netgear has indicated that this wouldn’t have been an issue if the victim had applied the firmware update the company released in 2016 for this very issue. “The flaw would let anyone gain remote access to its routers because Netgear wasn’t asking for any form of authentication via FTP, which was enabled by default.”
Worse, Shodan makes it easy for literally anyone take advantage of the fact that router manufacturers continue to still don’t take security too seriously, which is why we still see things such as hardcode passwords, embed backdoor accounts, or leave default credentials in use without forcing user changes upon implementation. “All of these “features” make it trivial for attackers to take over hundreds of thousands of routers at once after they learn about these vulnerabilities.”
The final insult in this scenario?
The adversary posted the sensitive documents for sale on a darkweb forum for a grand total of $150 - $200.
Lessons learned?
-
Patch your firmware, and ensure that default credential are NOT enable on Internet-facing assets
-
Use Shodan the way your adversary would, do not leave the outcomes to chance. Search Shodan for your organization before someone else does it for you!
Shodan provides a few different access models, there is definitely free access but with limitations.
The corporate API access model (three tiers: freelance, small business, corporate) will allow you to explore the Internet visually, download search results to your computer, enrich data, scan on demand, monitor your network in real time, use the developer API in an unlimited mannner. Enterprise access additionally give you bulk downloads, the firehose, Internet scanning, custom saurveys, and historical insights.
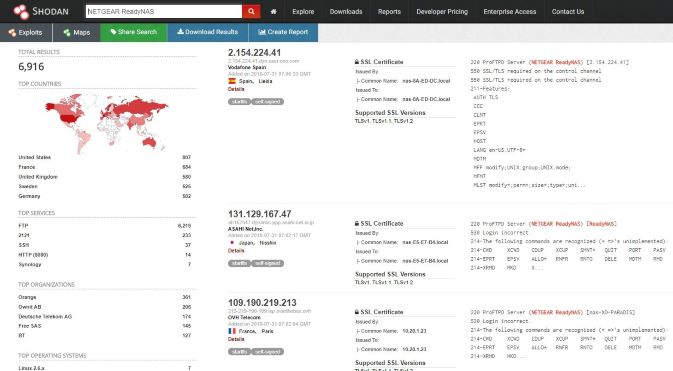
The Shodan web portal allows excellent filters and enables you to get started with great ease. Search query fundamentals will quide you through the basics. In keeping with our point of discussion, a query such as NETGEAR ReadyNAS yields 6916 immediate results, all answering on FTP, as seen in Figure 1. That doesn’t imply that their configured with default credentials but it does give you a sense of how pervasive Internet availability can be.
NOTE: Do not treat this as an opportunity to test credentials, unauthorized access is just that, don’t get yourself in trouble. Test only against assets and ranges for which you are authorized.
Figure 1: Shodan Web UI
While a web UI is nice and will pique your interest, if you really want to put the power of Shodan to good user you’re going to want to use the API. Shodan Developer readies you for easy integration and automation to generate reports, notify you of findings, or keep track of results over time. You can also subscribe to events in real-time for immediately response to new discoveries. Prefer the command-line? “The Shodan command-line interface exposes most of the API in a user-friendly way so you can access the Shodan database without needing to write your own scripts.” There are libraries to enable your use of the API via Python, Ruby, PHP, C#, Go, Haskell, Java, Node.js, Perl, PowerShell, and Rust. “But Russ,” you say, “what about R?” Bob Rudis to the rescue…again. Yep, there’s an R package for that. Install Bob’s R package interface to the Shodan API as follows:
devtools::install_github("hrbrmstr/shodan")
Important: You’ll be much happier using this package if your API key is stored in your .Renviron file. You really shouldn’t hard code it in your scripts. The Shodan R GitHub repository and post on Data Driven Security give you some good examples to to get started with, and confirm that you’re actively engaging the API via R. Returning to our Netgear ReadyNAS example, I’ve modified Bob’s map visualization for your experimentation.
# Created from Bob Rudis @hrbrmstr The New and Improved R Shodan Package
# http://datadrivensecurity.info/blog/posts/2015/Aug/the-new-and-improved-r-shodan-package/
library(shodan)
library(tibble)
library(data.table)
library(leaflet)
library(htmltools)
# Place your Shodan API key in .Renviron
# Uncomment for API testing and experimentation
#packageVersion("shodan")
#shodan_ports()
#shodan_protocols()
#resolve("google.com")
#reverse("172.217.3.110")
#query_tags()$matches
#shodan_query_list()$matches
netgear_ftp <- shodan_search("NETGEAR ReadyNAS")
netgear_ftp$total
colnames(netgear_ftp$matches)
for_map <- as.data.table(netgear_ftp$matches$location,
ip=netgear_ftp$matches$ip,
isp=netgear_ftp$matches$isp,
org=netgear_ftp$matches$org,
data=netgear_ftp$matches$data,
stringsAsFactors=FALSE)
# Uncomment if you want to write your results to a CSV
#write.csv(for_map, file="C://tmp//map.csv")
leaflet(for_map, width="600", height="600") %>%
addTiles() %>%
addCircles(data=for_map, lng=~longitude, lat=~latitude,
popup=~sprintf(htmlEscape(org)))
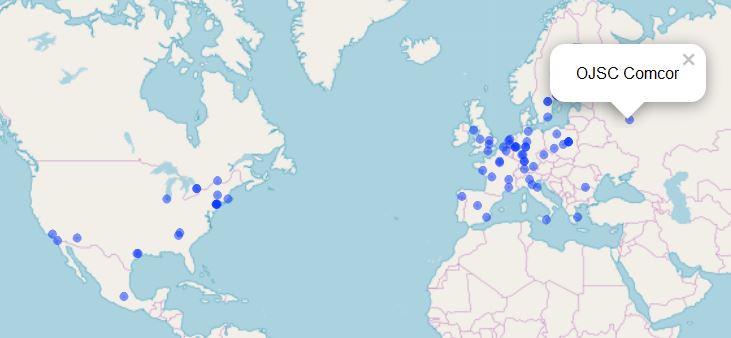
The result is an interactive map that highlights the first 100 Internet-exposed ReadyNAS systems across the world as returned by the Shodan API, as seen in Figure 2.
Figure 2: Shodan API result visualization
There are numerous ways to interact with this data. Use the org filter to define searches by your organization and have at it.
No one wants their data out on a dark web forum for a mere $150, avoid such challenges and proactively utilize Shodan as part of your prevention plan.
Cheers…until next time.